Companies invest in Salesforce integration services with a simple goal of connecting systems and processes. You want your systems to talk to each other, teams to work faster, and customer data in one place. Simple enough, right?
But here’s the part nobody really thinks about in the beginning. Every integration you set up is also a door. And if that door isn’t locked properly, someone on the outside will eventually try to walk through it.
We’ve already seen what happens this year when businesses left those doors unguarded. The cost wasn’t just financial; it was lost trust, headlines, and sleepless nights for leadership teams.
That’s why when you plan to hire Salesforce integration service experts, the conversation has to be about more than just connecting platforms. It has to be about connecting them securely.
Why is integration security under the spotlight
Let’s take a quick reality check. In 2025 alone, several global brands had sensitive Salesforce data exposed. It didn’t happen because Salesforce itself was broken. It happened because attackers took advantage of integrations.
In one case, employees were tricked into downloading a fake version of Salesforce’s Data Loader. Once installed, it looked normal on the surface, but in the background, it was quietly moving data out.
In another case, a trusted third-party platform was compromised. The attackers got hold of OAuth tokens and used them to slip into Salesforce environments across multiple companies.
These stories are a reminder of something most of us forget.
Integrations are powerful, but they also carry privilege. When you connect an app or system, you’re often handing over the keys to valuable data. If those keys are too broad or never expire, you’ve given attackers exactly what they need.
Where businesses fall behind
From what we’ve seen, data breaches linked to Salesforce integrations rarely come from one big mistake. They come from a series of small ones:
- A connected app is given more permissions than it really needs.
- A vendor app is installed without proper security checks.
- API activity isn’t monitored, so suspicious spikes go unnoticed.
- Tokens are set to last forever and never get rotated.
- An admin gets tricked by a convincing phone call or email.
Individually, none of these feels like a red-alert problem. But string them together, and you’ve got a direct path to a breach.
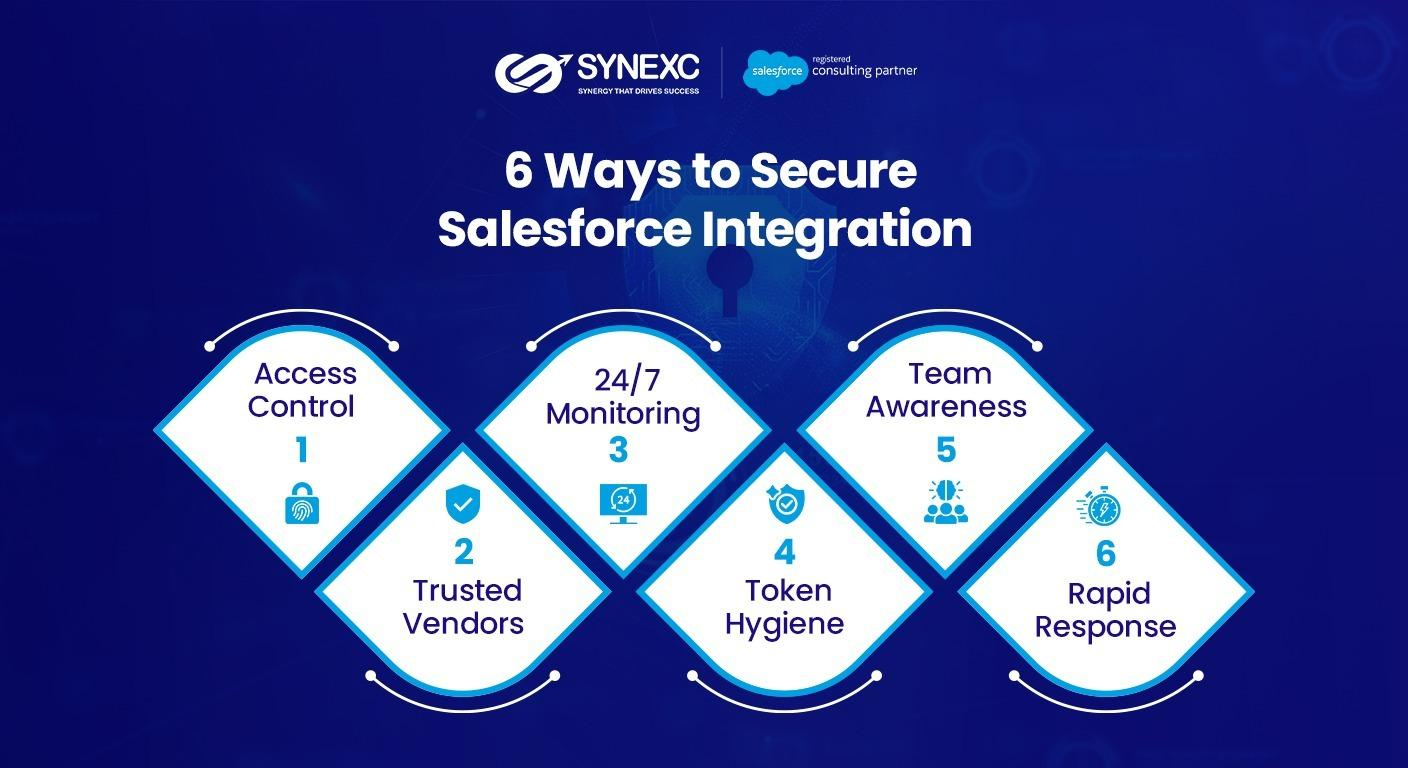
What secure Salesforce integration looks like
So, now the question is, how do we make sure our integrations don’t turn into weak spots?
Here’s what we put in place whenever we deliver a Salesforce data integration service for our clients.
-
Keep permissions lean
If an integration only needs lead data, that’s all it should have. Don’t hand over access to accounts, cases, and opportunities “just in case.” Every extra permission is another risk.
-
Choose vendors carefully
Before you approve a third-party app or platform, ask a few simple questions. How do they encrypt data? How long do their tokens live? Do they rotate keys regularly? A serious vendor will have answers ready.
-
Strengthen authentication
Multi-factor authentication is a must, but not all MFA is equal. Where possible, use stronger options like security keys. They make it much harder for someone to bluff their way past your defenses.
-
Watch what’s happening
Salesforce gives you the ability to log and monitor activity, but you have to use it. Keep an eye on API calls, connected app usage, and large data exports. If something looks unusual, investigate before it becomes a crisis.
-
Clean up your tokens
Think of tokens like spare keys. If you’ve given some out over the years and never collected them back, you probably don’t know how many are floating around. Rotate them regularly, and revoke the ones you don’t need anymore.
-
Train your people
Technology alone won’t save you. Many of this year’s breaches started with social engineering—someone on the inside was tricked. Training employees, especially admins and help desk staff, to slow down and verify requests makes a huge difference.
-
Be ready to respond
Even with strong defenses, things can go wrong. That’s why every company should have a clear response plan. Know who revokes tokens, who alerts customers, and how quickly systems can be restored. The faster you move, the smaller the damage.
Working with the right partner
If you’re planning to hire Salesforce integration service providers, make sure security is part of the pitch. A good partner won’t just say “yes” to every integration request.
They’ll also ask the hard questions: Do we really need this level of access? What’s the best way to monitor it? How do we shut it down fast if something looks off?
The right partner will:
- Build integrations with least-privilege access by default.
- Audit connected apps before they go live.
- Set up monitoring so you’re not flying blind.
- Train your team so they can manage integrations safely long-term.
In short, they’ll leave you with more than just working connections. They’ll leave you with confidence.
Security is not a one-time job
One of the biggest myths we run into is the idea that security is a project. You do it once, tick the box, and move on. The reality is different. Permissions need reviewing, tokens need rotating, employees need refreshers, and vendors need re-evaluating.
The companies that handled recent incidents well weren’t the ones that had perfect setups. They were the ones who treated security as ongoing maintenance, not a single milestone. That mindset made all the difference.
Wrapping it up
Summing up, Salesforce integration, while powerful, can expose you to vulnerabilities. So, adhering to the security best practices and partnering with a Salesforce integration partner is the key to staying secure.
And if you’re looking for a partner, don’t just settle for someone who can connect your systems quickly. Work with a team that treats security as part of the process. That’s what true Salesforce integration services should deliver.
And when you’re ready to build integrations that are seamless and secure, our Salesforce data integration service team is here to help. Let’s connect!
About the Author
Sambhav Arora is a 7X Certified Salesforce Consultant and CEO at Synexc, helping organizations unlock practical value from Salesforce with scalable, production-ready AI strategies.
FAQs
Q1. What are the most common causes of Salesforce integration breaches?
Weak permissions, unmonitored APIs, compromised tokens, and careless vendor checks often open the door to breaches.
Q2. How often should Salesforce integration tokens be rotated?
Ideally, every 90 days, or sooner if suspicious activity is detected.
Q3. How can a Salesforce partner help secure integrations?
As integration consultants, we make sure your integrations are safe from day one, setting the right access, monitoring activity, and guiding your team to prevent breaches.